
On June 3rd, 2022, MetaMask discolosed a serious clickjacking vulnerability discovered by the white hat group, United Global Whitehat Security Team(UGWST). This was a browser extension-only vulnerability, it allowed attackers to deceive users into giving sensitive information or sending crypto-assets without them realizing it. This was made possible since the MetaMask extension could be run as a hidden layer on top of another website. Due to the popularity of MetaMask, once this vulnerability was disclosed, we immediately recreated this vulnerability to further study and research the impacts of this vulnerability.
Our security team alerted those affected as quickly as possible and advised them on how to remedy this issue. We’re releasing our findings on this Clickjacking vulnerability to help other projects avoid making the same issue.
Vulnerability Analysis
Since MM did not provide a full explanation when it published this Clickjacking vulnerability, I ran into many obstacles when I attempted to duplicate it (various blind guessing vulnerabilities).They merely described the exploitation scenario and potential damage. So in order for everyone to grasp a better understanding of this vulnerability, I will first provide some additional information before starting my analysis.
Let’s first learn about Manifest- Web Accessible Resources. There is a configuration in the browser extension wallet, web_accessible_resources, which is used to restrict which resources the web page can access the browser extension. By default, the web page cannot access the resource files in the browser extension, only the browser extension itself can access the resources of the browser extension. In short, pages under protocols such as http/https cannot access chrome-extension by default. However, if the extension wallet is configured with web_accessible_resources to expose the resources inside the extension wallet, it can be accessed by protocols such as http/https.
The version of the MM extension wallet before 10.14.6 (we’re using 10.14.5 as an example) has always retained “web_accessible_resources”: [“inpage. js”, “phishing.html”] configuration, and it’s the main reason why this vulnerability can be exploited.

However, during our analysis, it was found that in app/scripts/phishing-detect.js (v10.14.5), the phishing page jump has been restricted by the protocol. (My understanding here is that there are other flaws. After all, “web_accessible_resources”: [“inpage. js”, “phishing. html”]` configuration is still preserved).

We continued to follow up on the time point of the change of this protocol restriction, and found that this restriction was added to the following commit, which means that before v10.14.1, because there was no restriction on the jump protocol, the Clickjacking vulnerability can be easily exploited.
Related commits:
https://github.com/MetaMask/metamask-extension/commit/c1ca70d7325577835a23c1fae2b0b9b10df54490
https://github.com/MetaMask/metamask-extension/compare/v10.14.0..v10.14.1 _
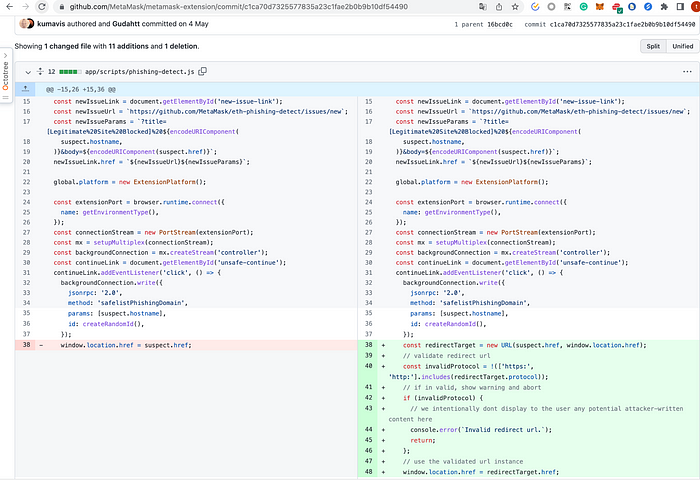
In order to verify the analysis process of the code, we switched to the version v10.14.0 before the protocol restriction for testing, and found that the entire vulnerability can be easily reproduced.

It is also worth mentioning that MM reported the Clickjacking vulnerability was fixed in v10.14.6, so v10.14.5 was still vulnerable. Let’s look back at this line here.
“web_accessible_resources”: [“inpage.js”, “phishing.html”]
After reading through the code, in v10.14.5 and previous versions of the code, when the phishing page is prompted, users can continue at their own risk. After that, this hostname will be added to the local whitelist list. So that the next time you visit the website, there will be no more reminders of MetaMask Phishing Detection.
For example, the phishing website, ethstake.exchange is embedded in the web page through the iframe tag. The malicious site can be added to the whitelist by using the Clickjacking vulnerability. At the same time, MM will not continue to pop up warnings the next time the user visits a phishing website.

Analysis Summary
During the analysis above, we discovered MM recently fixed two clickjacking vulnerabilities. During the reproduction process, it was found that the latest v10.14.6 has removed the relevant configuration of web_accessible_resources, and completely repaired the clickjacking problem of the MetaMask Phishing Detection page.
(1 ) The fix for using the Clickjacking vulnerability to induce users to transfer money (affected version: <= v10.14.0 ) :
https://github.com/MetaMask/metamask-extension/commit/c1ca70d7325577835a23c1fae2b0b9b10df54490
(2 ) Fix the use of Clickjacking vulnerability to add phishing website to the whitelist (affected version: <= v10.14.5 ) :
https://github.com/MetaMask/metamask-extension/commit/7199d9c56775111f85225fe15297e47de8e2bc96
We performed the Clickjacking vulnerability detection on other well-known extension wallets in the chrome extension store, and found that the following wallets are affected by the Clickjacking vulnerability.
- Coinbase Wallet (v2.17.2)
- Coin98 Wallet (v6.0.6)
- Maiar DeFi Wallet (v1.2.17)
Our security team reached out to the affected teams, but not all parties have provided feedback. It has been 13 days since MM disclosed this vulnerability. In order to prevent users from falling victim to this vulnerability, we decided to release our findings in this article. If you’re currently using the wallets mentioned above, please reach out to the team to have them solve these issues immediately. If any of the projects mentioned above have any questions or need assistance, feel free to reach out to our security team. We’re more than happy to help.
Once again, we remind developers of browser extension wallets to check whether they are affected by this vulnerability, especially if it’s developed based versions of MetaMask <v10.14.6. Feel free to reach out if you need any assistance.
We also advise users of these wallets to stop using these extension wallets (and close them in your extension) until the team has resolved the issues. Users can update to use the patched version once the team releases the updated version.
Reference link: https://medium.com/metamask/metamask-awards-bug-bounty-for-clickjacking-vulnerability-9f53618e3c3a
