
On August 10, 2021, according to the news from the SlowMist Zone, the cross-chain interoperability protocol Poly Network was attacked by hackers. The SlowMist security team immediately cut into the analysis and shared the analysis results as follows.
The details of the attack
1. The core of this attack is that the verifyHeaderAndExecuteTx function of the EthCrossChainManager contract can execute specific cross-chain transactions through the _executeCrossChainTx function.
2. Since the owner of the EthCrossChainData contract is the EthCrossChainManager contract, the EthCrossChainManager contract can modify the keeper of the contract by calling the putCurEpochConPubKeyBytes function of the EthCrossChainData contract.
3. The verifyHeaderAndExecuteTx function of the EthCrossChainManager contract can perform user-specified cross-chain transactions by calling the _executeCrossChainTx function internally. So the attacker only needs to pass in the carefully constructed data through the verifyHeaderAndExecuteTx function for the _executeCrossChainTx function to execute the call to the EthCrossChainData contract PutCurEpochConPubKeyBytes function to change the keeper role to the address specified attackers.
4. After replacing the address of the keeper role, the attacker can construct a transaction at will and withdraw any amount of funds from the contract.
Process
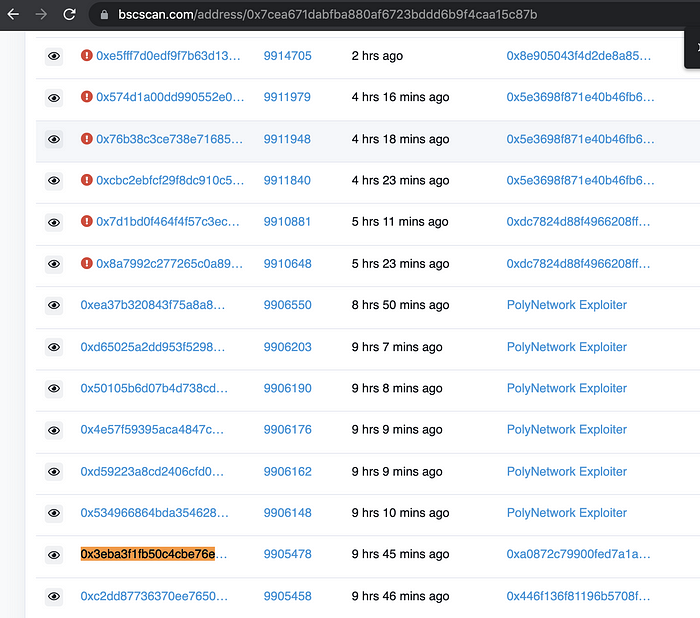
1. Attacked contract:
https://bscscan.com/address/0x7cea671dabfba880af6723bddd6b9f4caa15c87b
2. The attacker used the verifyHeaderAndExecuteTx function of the EthCrossChainManager contract to call the putCurEpochConPubKeyBytes function to change the keeper operation:
https://bscscan.com/tx/0x3eba3f1fb50c4cbe76e7cc4dcc14ac7544762a0e785cf22034f175f67c8d3be9
3. Attack transactions:
https://bscscan.com/tx/0x50105b6d07b4d738cd11b4b8ae16943bed09c7ce724dc8b171c74155dd496c25
https://bscscan.com/tx/0xd65025a2dd953f529815bd3c669ada635c6001b3cc50e042f9477c7db077b4c9
https://bscscan.com/tx/0xea37b320843f75a8a849fdf13cd357cb64761a848d48a516c3cac5bbd6caaad5
4. After the attack was completed, the keeper was modified, causing other normal transactions to be reverted.
5. The same operation on Ethereum:
Attacked contract:
https://etherscan.io/address/0x838bf9e95cb12dd76a54c9f9d2e3082eaf928270
The attacker Changes the keeper operation:
https://etherscan.io/tx/0xb1f70464bd95b774c6ce60fc706eb5f9e35cb5f06e6cfe7c17dcda46ffd59581
The Transaction that the attacker carried out the attack:
https://etherscan.io/tx/0xad7a2c70c958fcd3effbf374d0acf3774a9257577625ae4c838e24b0de17602a
Summary
This attack is mainly because the keeper of the EthCrossChainData contract can be modified by the EthCrossChainManager contract, and the verifyHeaderAndExecuteTx function of the EthCrossChainManager contract can execute the data passed in by the user through the _executeCrossChainTx function. Therefore, the attacker uses this function to pass in carefully constructed data to modify the keeper of the EthCrossChainData contract. It is not the case that this event occurred due to the leakage of the keeper’s private key.
